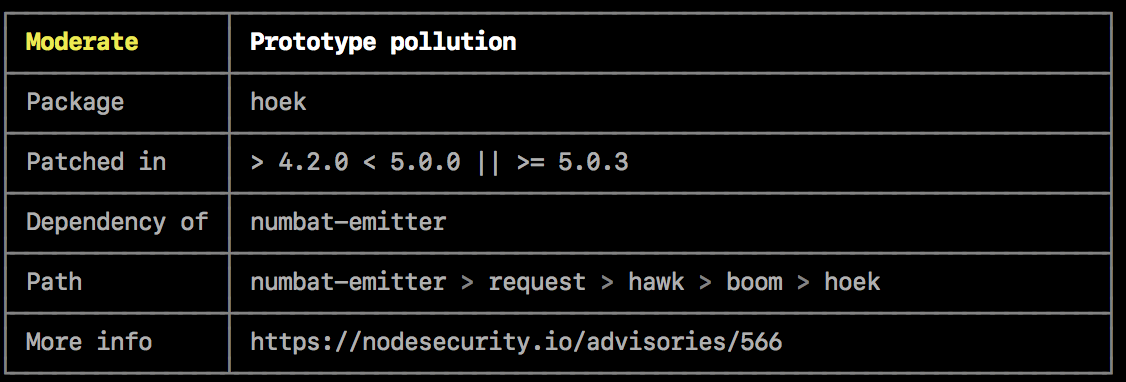
Audit reports contain tables of information about security vulnerabilities in your project's dependencies to help you fix the vulnerability or troubleshoot further.
The severity of the vulnerability, determined by the impact and exploitability of the vulnerability in its most common use case.
Severity Recommended action Critical Address immediately High Address as quickly as possible Moderate Address as time allows Low Address at your discretion
The description of the vulnerability. For example, "Denial of service".
The name of the package that contains the vulnerability.
The semantic version range that describes which versions contain a fix for the vulnerability.
The module that the package with the vulnerability depends on.
The path to the code that contains the vulnerability.
A link to the security report.